DTRA ITSS Case Study

What We Do
TekSynap provides DTRA with incident response analysts, computer crime investigators, incident handlers, incident responders, incident response coordinators, incident response analysts and intrusion analysts as well as other cybersecurity personnel as part of our solution to meet the requirements of the ITSS program. Our Cyber Hunt activities include collection of intrusion artifacts, correlating incident data for root cause analysis and vulnerability mitigation, and coordination and support of enterprise-wide Computer Network Defense incident resolution.
Methodology and Processes
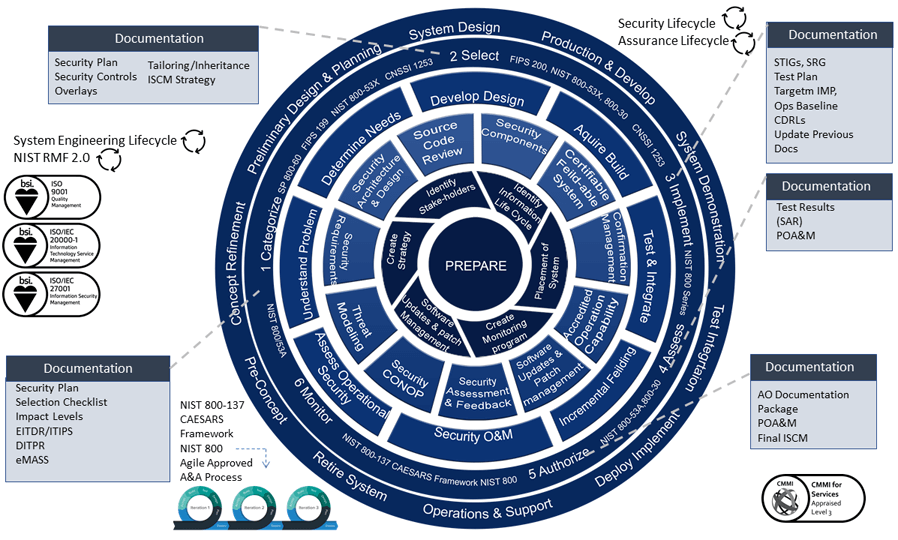
To support DTRA’s Cyber Hunt requirements, TekSynap conducts cyber threat horizon analyses. Our approach identifies existing risks and vulnerabilities and uses our mission knowledge and cyber threat data from sources such as USCYBERCOM to help predict and defend against potential vulnerabilities and develop proactive responses. Most vulnerabilities result from a combination of interactions and gaps between people, existing processes, and technology. We analyze and monitor these interactions other advanced persistent threats (APTs) for risk, drawing on our experience in conducting risk assessments and vulnerability management activities. At program onset, we conduct a comprehensive assessment identifying risks and prioritizing them by severity and probability, identifying proposed mitigation strategies and then presenting the post-mitigation picture, which we then place in a continuous feedback loop.
People in Action
TekSynap provides team members for all four of DTRA’s simultaneously running cybersecurity processes, including CSSP Detect, Response, Protect, Sustain, and Incident Response/Cyber Hunt. TekSynap manages a team that provides 24x7x365 support and provides support after hours and on weekends as required. We also provides guidance on incident resolution, including of possible CSSP intrusions and spillages. Our team also ensures effective collaboration with other teams and has proven experience in working with Insider Threat, System Administrators, Infrastructure, Engineering, etc. to accomplish CSSP goals. TekSynap has the proven ability to lead the CSSP so that the agency passes all inspections/ audits, including the Evaluator Scoring Metric (ESM) and Cyber Protect Team (CPT).
Compliance and Standards
TekSynap employs ISO 9001, ISO/IEC 20000, ISO 27001, and PMBOK best practices across all programs we support, including DTRA. These practices are instituted in our corporate quality management systems and program charters. Additionally, our Cyber Hunt activities require compliance with the DoD Directive 8000.01, DoD Instruction 5205.13, DoD Instruction 8500.01, DoD Instruction 8530.01, and DoD Instruction DoDI 8551.01 and other applicable DoD cyber regulation. In addition, TekSynap incorporates NIST Special Publications 800-30, 800-37, 800-39, 800-70, and 800-94 into its regulatory compliance framework. Finally, our Cyber Hunt activities are compliant with the Chairman of the Joint Chiefs of Staff Manual (CJCSM) 6510.01B detailing the Cyber Incident Handling Program.